Now you can enhance network security and employee productivity with an additional layer of protection. Web Protection & Content Filtering is our easy-to-manage web security feature that allows you to control, monitor and enforce client web policies all via a single pane of glass.
Robust, flexible, easy to manage
- Keep your business safe and end-users protected by securing against websites pushing malware, phishing, proxies, spyware, adware, botnets and spam
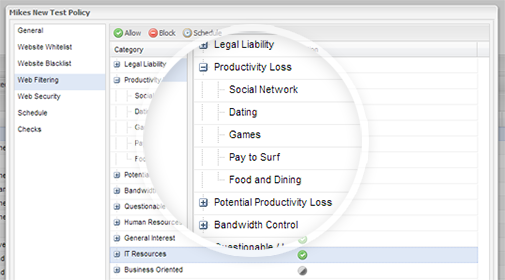
- Apply time-based browsing rules and web content filtering policies across a robust range of website categories. This helps to reduce non-work related browsing such as social networking, auctions, games and more
- Help employees stay productive with common-sense web browsing policies designed for the workplace
- Stay on top of bandwidth usage with alerts when devices exceed thresholds – enabling quick remediation to avoid unwanted costs or a throttled network
- Protect the business from legal liability. Reduce the risk of a security breach through proactive internet access controls
Here’s how Web Protection & Content Filtering Works
The Web Protection feature is built around a policy-driven approach so each device that you turn on for Web Protection will point to a central policy. You can edit the policy and adjust settings for the devices with that particular policy. This helps scale Web Protection to a range of devices as opposed to having device-level settings across the board.
There’s a ton of great policy options
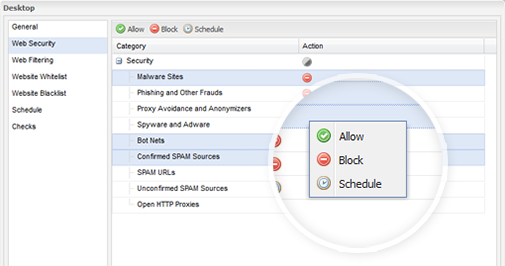
- Block users from visiting suspected and confirmed unsafe sites
- Apply web filtering to enforce internet access policies in the workplace
- Set white lists and black lists to override category based filters
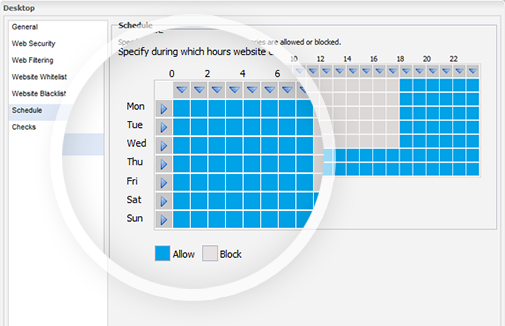
- Optionally apply a schedule so employees can access non-work sites during out of office hours or on the lunch hour
- Apply a ‘web bandwidth’ check and be alerted when there’s excessive bandwidth activity on a network
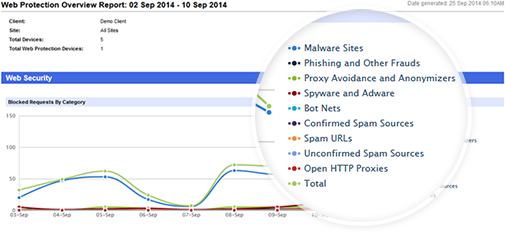
- Intelligently filter internet activity by day, category and URL to reveal trends, spikes and irregularities. Show or hide URL data depending on data privacy requirements
… complete with detailed reporting tools that let you analyze browsing activity and demonstrate the effectiveness of web security.